10 criteria to choose a VPN Provider
Here are the 10 most impactful criteria in choosing a best VPN provider to meet your privacy and torrent needs.
VPN Providers and how to find the best VPN service to fit your privacy and torrent needs based on 10 criteria
1. Global Surveillance
Networks in certain nations are more surveilled than others. VPN server locations in these surveilled networks have more exposure to capabilities that are able to capture your traffic. These capabilities are on the military defense and state secret level, and ostensibly targeted on activities related to that level. Your consideration for using VPN servers in these locations are that national defense agencies could probably have access to your traffic. If you are comfortable with sharing your traffic with these agencies, then this is not a concern. If this troubles you, then you should use a VPN server in a different location outside of these five eyes and 14 eyes nations. 'Five Eyes' nations and '14 Eyes' nations have more surveillance methods and sharing agreements to turn over records and logs to their counter parts.
'Five Eyes' Nations
Australia, Canada, New Zealand, United Kingdom, United States
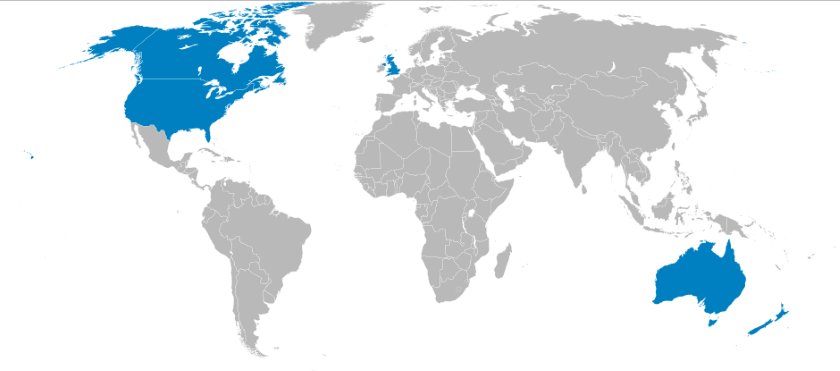
'14 Eyes' Nations and Sharing Partners
Denmark, France, the Netherlands and Norway
Germany, Belgium, Italy, Spain and Sweden
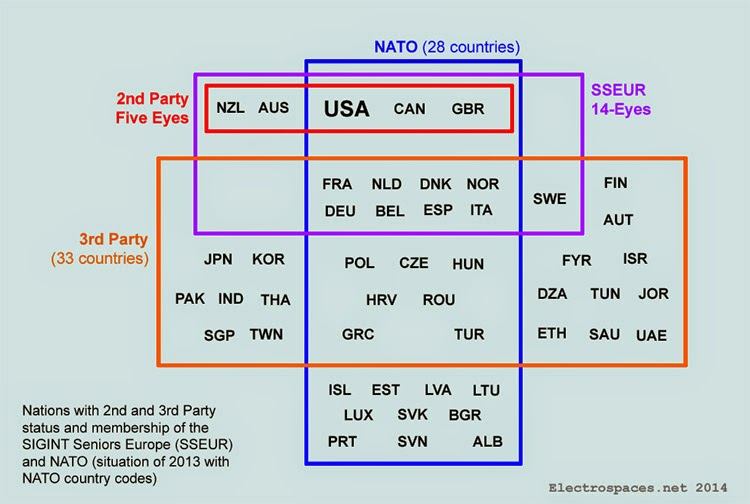 Image courtesy of Electrospaces.net 14-Eyes are 3rd Party partners
Image courtesy of Electrospaces.net 14-Eyes are 3rd Party partners
2. Jurisdiction and Logs
The nation your VPN provider is based in will determine how easily that provider can be compelled to hand over it's logs and your data to court ordered requests. Nations that produce a great deal of media, like the United States and the EU, typically have strong data retention and copyright laws that make it hard for providers in those nations to deny requests for your data. Thus making them a poor choice for being your VPN Provider's home base. It is important you understand what data of your's the provider stores as well as what activity of your's they log. Many of them claim they store 'No Logs Ever', and it is up to you to figure out what that actually means. Most server activity generates some kind of log. You want a VPN that specifically states they do not log any of your outbound traffic or outbound network activity, and ideally they don't even log your connection attempts, usually it will require them to make some proprietary adjustments to not log your connection attempt because that information is needed for troubleshooting connection errors and usage. The best practice is when a VPN runs their entire server in ram-disk or memory, such that if the server is turned off, all information is immediately lost and those logs never hit a disk in the first place.
3. Speed
A good VPN should not impact your normal bandwidth or latency by more than 20%. If your network connection performance on either bandwidth or latency is over 20% slower, then it is time to choose a new provider. This is a great resource to test bandwidth and this a torrent link to test torrent speed
4. Customer Support
Email and chat support with 6 hour turn around is standard. Also standard are well written connection and client setup guides in a public on-line knowledge base. Before you purchase, make sure you review those setup guides and that you feel comfortable with all the install and configuration steps. If they look ton complicated, move to a different provider, there are plenty that offer very easy setups, even for non-technical users.
5. Connection Technology, Protocols and Client Application Support
A good VPN will support at least 3 different types of standard connection protocols and allow you to connect with open-source clients in addition to any proprietary client apps they build themselves. Forcing users to only use their client application is a bad sign. You are paying for a back-end service and should be able to connect to it through a client of your choosing rather than be forced to install software that you aren't allowed to see inside it's source code.
Minimum set of protocols:
- OpenVPN, this is a very common protocol in the industry and has several open source client available for you.
- L2TP, this protocol has a client built-in to many different operating systems and devices. It can readily be used without any software installation.
- IKE2, this is a more secure protocol than L2TP and has the advantage that newer iOS, Windows and OS X devices have clients for it built in. (No Android native support)
Client links:
- strongSwan Open source client that runs on Linux 2.6, 3.x and 4.x kernels, Android, FreeBSD, OS X, iOS and Windows
- OpenVPN Uses the OpenVPN protocol and works great on Windows and Linux
- Tunnelblick Open source client for the OpenVPN protocol and runs on OS X and macOS
6. Privacy Ethics and Transparency
Their website should protect your privacy by not loading any 3rd Party cookies or using 3rd party tracking analytics. They should also honor the 'Do Not Track' flag cookie. And they should have privacy policy that states what they do with data and who owns it. Make sure you read their privacy policy carefully and you review what tracking cookies they use. Here's how to check the cookies in Chrome
The difference in a site that does not use 3rd party tracking cookies versus a site that does is shown below.
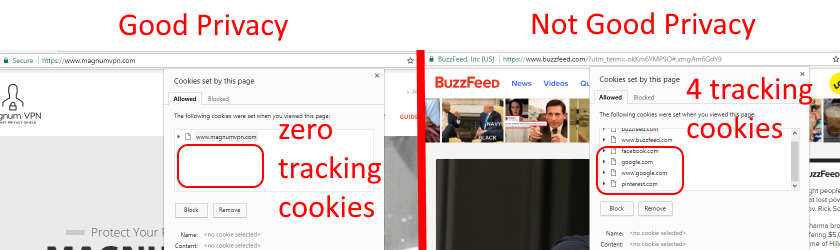
There are also browser plug-ins that will help show and block trackers, here is an example of Avira's plug-in blocking and counting 3rd party trackers.
![]()
7. Server location
Server Location is important in 4 scenarios:
- Proximity for performance, in this case you want a server close to you, at least on the same continent, in order to get the best speed performance possible.
- Physical Jurisdiction, in this scenario you want to choose a server that is in a country where you are comfortable in the event that law enforcement seizes that server from the provider.
- Network Surveillance, if you are concerned about global surveillance mentioned in criteria #1, then you want to avoid servers in 14 eyes countries and their partners.
- Bypassing Geo-restrictions, if certain websites or VOIP applications are blocked in your local region, you will want to choose a VPN server location in a region that is not blocked. This is an effective way of bypassing geo based restrictions.
8. Price and connection limits
Typical monthly prices range from $3 to $10 and this usually allows for multiple simultaneous connections so that you can use multiple devices on a single account. Avoid 'Free' VPN providers, many free VPN providers make it unclear who actually owns and operates the service. This makes it difficult to trust they they are properly shielding your privacy.
9. Payment Options
Many providers are now accepting payments via Bitcoin, this is an added privacy feature that allows you to pay for service using an identity abstracted Bitcoin wallet. It is very easy to create a Bitcoin wallet using an email address that is not linked to your personal identity. Using this method for payment means the VPN provider won't be storing any of your personal information or identity.
10. Offer DNS and DNSCrypt
Most providers offer their own DNS servers which you will absolutely want to use. It defeats the purpose of a VPN if you still use your ISP's DNS servers. Some even offer DNSCrypt-Proxy 2 which is like HTTPS for DNS, it encrypts your DNS traffic and it protects against DNS spoofing. Which is very important protection to have when using public wifi.

